
Experienced network intruders and ransomware groups have struck an alliance helping each other monetize their skills by spreading malware to company networks.
One access-as-a-service provider works with multiple ransomware collectives, including REvil/Sodinokibi, offering them access to large targets.
Symbiotic relationship
High-profile ransomware actors like REvil focus on companies and are in constant need of new victims to keep the business humming.
Experts in breaching corporate networks advertise their talent on underground markets or over secure messenger communication and are the perfect partner.
Intruders hack into the network of a company and then rent or sell access to a ransomware team. This mutually beneficial cooperation enables spreading file-encrypting malware even on more secure networks.
Research from Advanced Intelligence (AdvIntel) reveals the strong connection between the two types of cybercriminal operations.
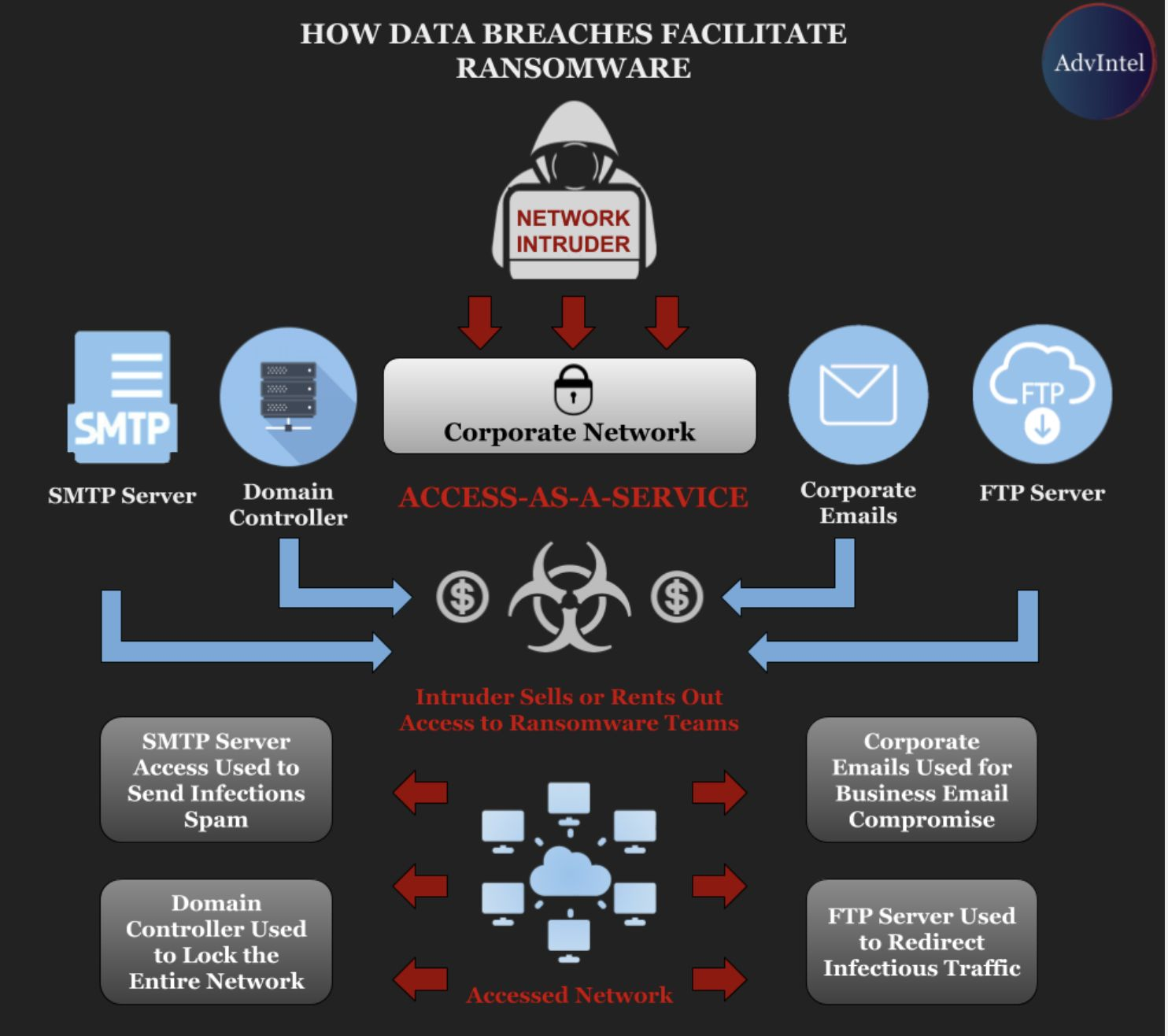
As seen in the image above, corporate network access can be leveraged for several nefarious businesses, including business email compromise and spam.
One particular hacker called -TMT- has been working with REvil operators since August 2019. The actor already had experience with this since they collaborated with other ransomware teams before, Yelisey Boguslavskiy, director of security research at AdvIntel, writes in a report today.
Becoming involved with the REvil aggregate was possible through Lalartu, a high-profile member of an underground forum that practically vouched for REvil developers when they picked up where GandCrab left.
Previously, Lalartu specialized in admin panel compromises, so they were familiar with the skills and offerings of other access providers, Boguslavskiy found.
Both Lalartu and -TMT- discovered the benefits of collaborating with ransomware groups and offered their services to high-profile syndicates.
"By June 2019, this was "truniger" collective for -TMT-, and REVil group for Lalartu. Eventually, Lalartu facilitated the connection between -TMT- and REvil, as -TMT-'s attack skills were in high demand by such collectives."
According to AdvIntel intelligence, -TMT- registered on an influential hacker forum in May but sources indicate that they have a history of operating for at least one year via secure messengers.
Access to hundreds of corporate hosts
Through June, July, and August, -TMT- advertised their corporate network compromises without giving any victim name.
The prices ranged between $3,000 and $5,000 for access to hundreds of hosts and servers from companies in different countries, operating in various industry verticals:
- Latin American house products provider operating in Chile, Bolivia, and Peru - 1069 hosts, 105 servers compromised
- Taiwanese meta manufacturer - 388 hosts,15 servers compromised
- Colombian financial services provider - 623 hosts compromised
- International maritime logistics services provider - 668 hosts compromised
- Network of US universities and educational institutions - 875 hosts, 87 servers compromised
- Danish dairy producer - 1 host, 72 servers compromised
- Bolivian energy sector company - 270 hosts, 12 servers compromised
The prices were influenced by the type of access offered and lower ones were for remote desktop (RDP) connections, which are easier to discover.
For one target, though, -TMT- was able to get full access to the administrative panels, server hosts, and corporate VPN networks. Access to all this was priced at $20,000.
AdvIntel received "extended evidence" of the breaches and in private conversations with the hacker learned that they "extracted admin credentials and can safely navigate through the network and elevate their access privileges as needed."
A sensitive target of this compromise is a server from the financial division storing valuable corporate information.
Buyers don't have to pay for full access. The hacker told AdvIntel that they were willing to upload malware into the system, or to open a single server access session for a lower price. This is an offer he makes to ransomware collectives, too.
AdvIntel's research also details the tactics, techniques, and procedures used by -TMT-, which include using Metasploit and the Cobalt Strike pentesting platform.
This symbiotic relationship proves the business acumen of both ransomware affiliates and network intruders. Both REvil and -TMT- are players in the big league that prosper from each other's talents.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now